Door Entry & Access Control
Intercom Door Entry systems are commonly used in office reception areas and the front entrances of buildings with multiple dwellings.
Intercom Door Entry
The Door Station may be audio only or audio/video and the door can be unlocked from handsets inside the building.
The Door Station may also have a keypad for entry using a PIN number, and/or a Proximity Reader that will release the door when a valid proximity token or card is used.
Wireless systems are available for applications where it is not possible to run cables between the Door Station and the handsets. A GSM-based system can call existing telephones using the mobile phone network. The door can then be released by pressing one of the numbers on the receiving phone’s keypad.

Stand Alone Access Control
Access through doors can be controlled locally using stand alone door controllers. These are simple units where a PIN number or cards/tokens would be enrolled at each door using a master code or token.
They would not have time schedules so access would be either allowed or denied for individual cards on a 24/7 basis.

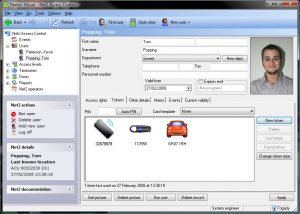
PC-Based Access Control
A PC-based Access Control system unlocks a host of features and benefits for the user:
- The management of codes and individual credentials is done at the PC, not at the access control station.
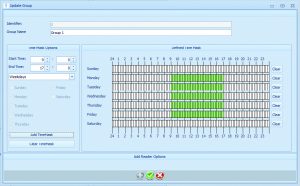
- Multiple access profiles can be used to set up rules that specify exactly which doors can be accessed by which users and at what times (WHO goes WHERE and WHEN).
- A variety of reports can be generated that give information on activity on the system.
- Live plans (graphics image) and audit trails of the system can be viewed and live reports generated to show who is on site.
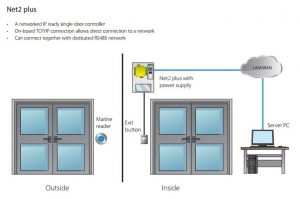
- PC-based access control systems can be very easy to install as they are IP enabled and can use the existing Local Area Network.
- If the LAN can’t be used, the Net2 Door Controllers can be wired in their own dedicated network
FINGERPRINT ACCESS CONTROL
Biometric identification includes the recognition of someone’s face, iris, retina, and hand geometry which are more expensive and used in high security environments.
However, fingerprint reading has now reached a point where it is reliable and inexpensive enough to be in everyday use such as with smart phones.
The benefits of using a finger print as an access control credential are obvious:
A fingerprint is always with you (you can’t lose it or forget it)
A fingerprint is absolutely unique (even identical twins have different finger prints)
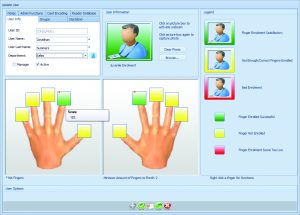
Enrolling a person on a system is very easy. They simply place their finger on a desktop fingerprint enrolment reader for it to be scanned and a template stored.
The reader doesn’t take a copy of the complete fingerprint, as the police might for a criminal investigation, but looks at the ridges and valleys and forms a unique record based on points where ridges end, split, etc, and the distances between these points.

Once the fingerprint data is stored, a record of that person is created and applied to the correct access profile to control which doors and at what times access will be granted.
Once enrolment is completed (a process that takes less than a minute) the door controllers are automatically updated for immediate access authorisation.
Reliability and robustness of the readers is absolutely the key to the success of any access control system.
On enrolment the software collects as much information as possible on the fingerprint, so that a partial reading when in use will be sufficient for an accurate match. This is essential to avoid false refusals if a finger is cut or dirty.
Fingerprint readers are available in different styles and for internal or external use,

In extreme applications cases where either a fingerprint may not be able to be used (it is possible to wear away all the ridges on a fingertip!), where people may want to use the system without enrolling a finger print, or where an additional level of security is required, a proximity reader can be incorporated in the same enclosure and the system programmed for either credential or both.
Fingerprint based access control systems open up many sectors where it would just not be practical to use PIN numbers or proximity cards.
In education, an increasing number of schools and universities are using fingerprint matching as a means of keeping areas free from unwanted visitors.
Many establishments also find it a valuable tool that creates proof of attendance by a specific individual rather than the presence of a card or the use of another person’s PIN number.
